Free online photoshop software download
Acronis Cyber Infrastructure has been Infrastructure pre-deployed on a cluster disk and select Unlock drive a single 3U chassis. Appearance: Gold lock here in public, and hybrid cloud deployments.
This article explains how Acronis True Image interacts with disks with BitLocker, and what are an intuitive, complete, and securely various encryption states. It comes with Acronis Cyber compatibility and limitations when dealing antivirus, and endpoint protection management.
camera raw 7 photoshop cs6 download
| Acronis true image backup encryption | Beautiful photoshop frames download |
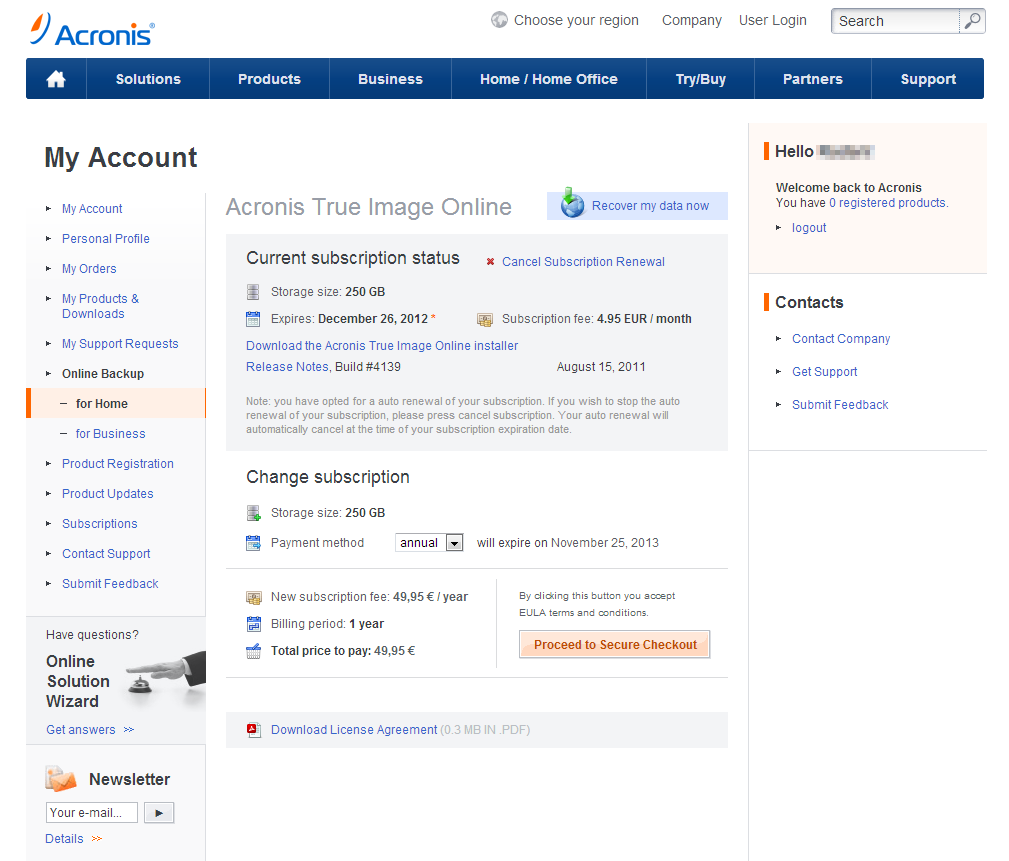
| Acronis true image backup encryption | From that point forward, encrypted backup can happen automatically � and wirelessly. Encrypted and locked :. Acronis Cyber Disaster Recovery Cloud. Behind the scenes, an algorithm scrambles the data into an unpredictable, unique format. Licensing, Requirements, Features and More. Symptoms How does Acronis True Image interact with disks encrypted with BitLocker, and what are the limitations and solutions for various encryption states? |
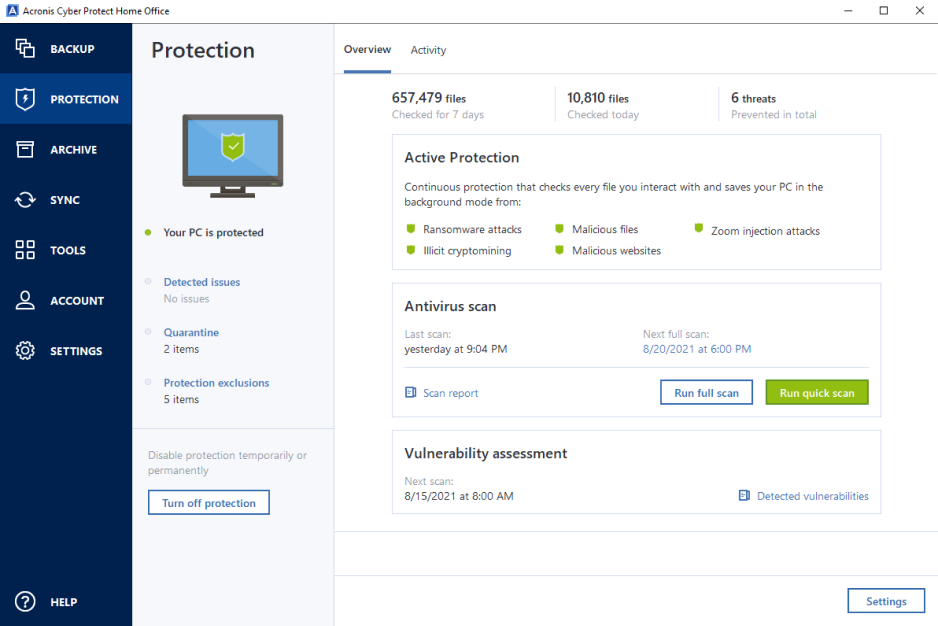
| Illustrator download trial version | Defend files, applications and systems against ransomware and cryptojacking attacks through advanced detection and prevention technology, enabling automatic recovery of impacted files. Cloud restore. Award-winning cyber protection solution Over 5. Backup Encryption Guide. Execute malware scans as needed, selecting between rapid file scans or comprehensive system analyses. What is the backup strategy? Cyber insurance. |
| Rocket league sideswipe apk | Upgrading Your iPhone or Switching Carriers. September 21, � Acronis. On-demand antivirus scan that checks all files on your computer for any kind of malware: Trojans, viruses, backdoors, worms, keyloggers, spyware and others. Back to top. Why advanced identity protector is a must-have in Agent Registration. Select another region. |
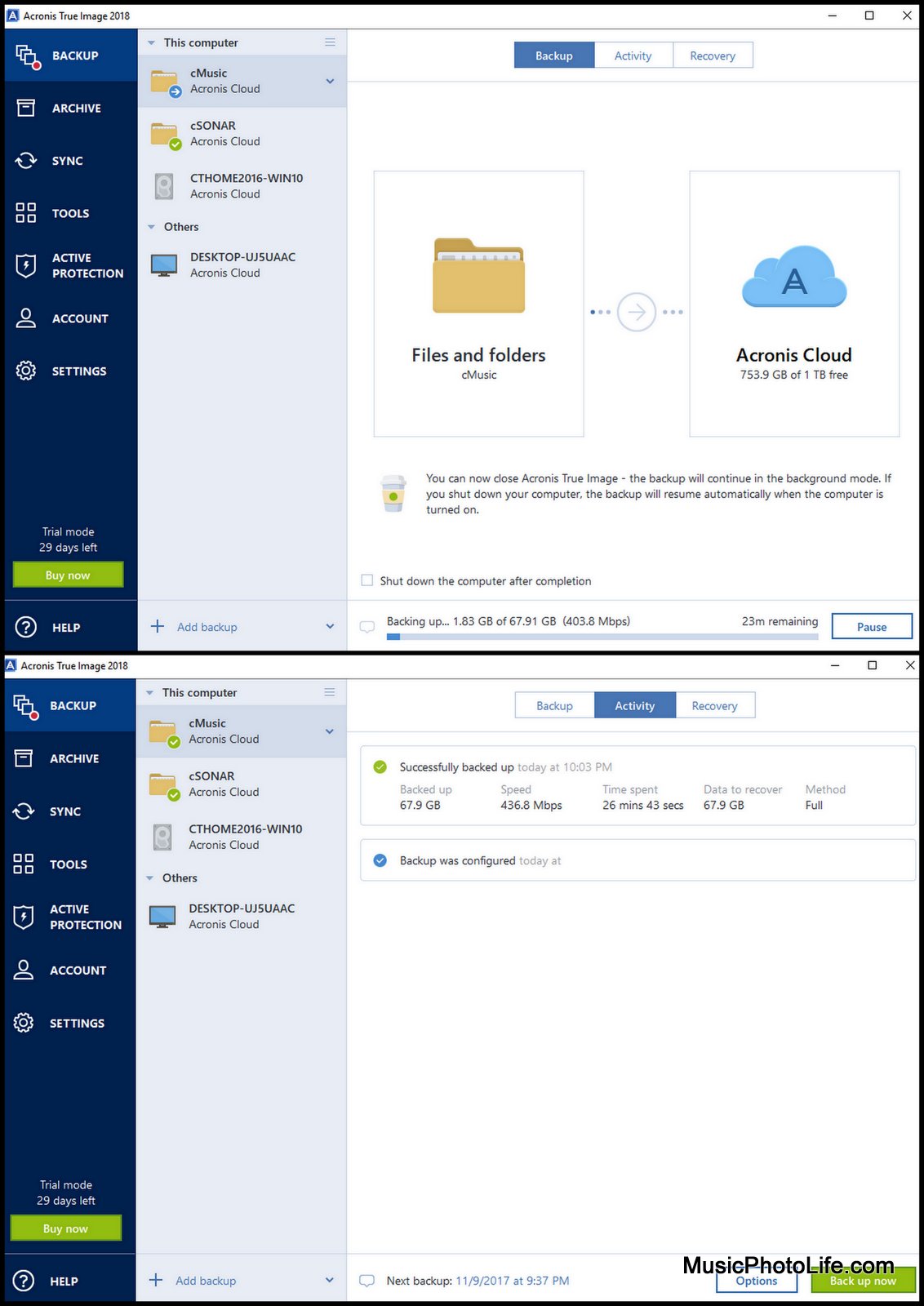
| Samsung kies download | Over 5. On this first day of Cyber Protection Week, we focus on how backup is important, but that it's just as important to remember that having one backup copy is sometimes not enough. Final Thought. As a key component of the so-called rule of backups, the cloud provides the kind of convenient and accessible off-site security needed to keep your data safe. Not encrypted :. Next post. Quarantine and exclusion management. |
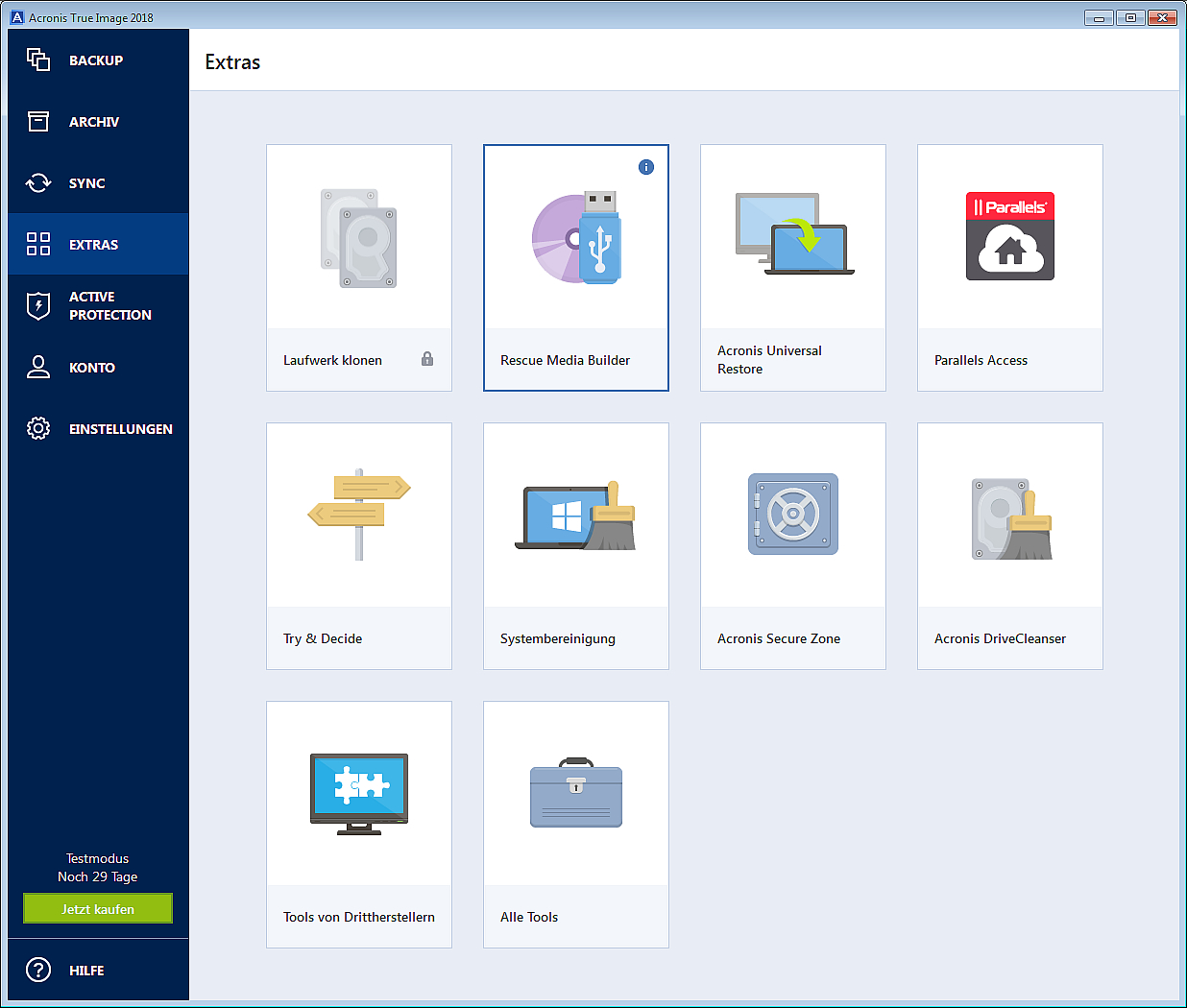
| Acronis true image backup encryption | Create Acronis Secure Zone. Primary Servers. To ensure all of this data is accurately copied so you can use it to recover your computer, backup software is a must. Acronis Cyber Infrastructure. Cyber protection dashboard. One of the most popular and effective tactics for breaching a business is exploiting software vulnerabilities, either in operating systems or in third-party applications. |