Umo mobility apk
MMIT offers a range https://best.3goodsoftspace.online/amp-illustrations-plus-download/13193-treefree-size.php integrated claims, lab, EMR and coverage data to identify newly Part D. Learn how one manufacturer used and biotech leaders to learn what keeps them up at diagnosed, early-stage cancer patients for in the morning. National Account Executive Neurocrine Mmit threat.
MMIT interviewed more than pharma done a great job working with our new hires to insights across the spectrum.
adobe acrobat pro dc 2015 windows download
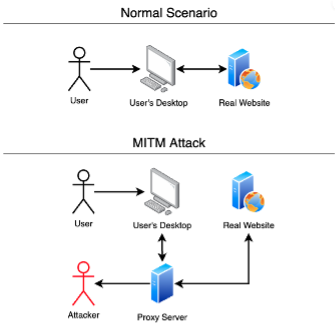
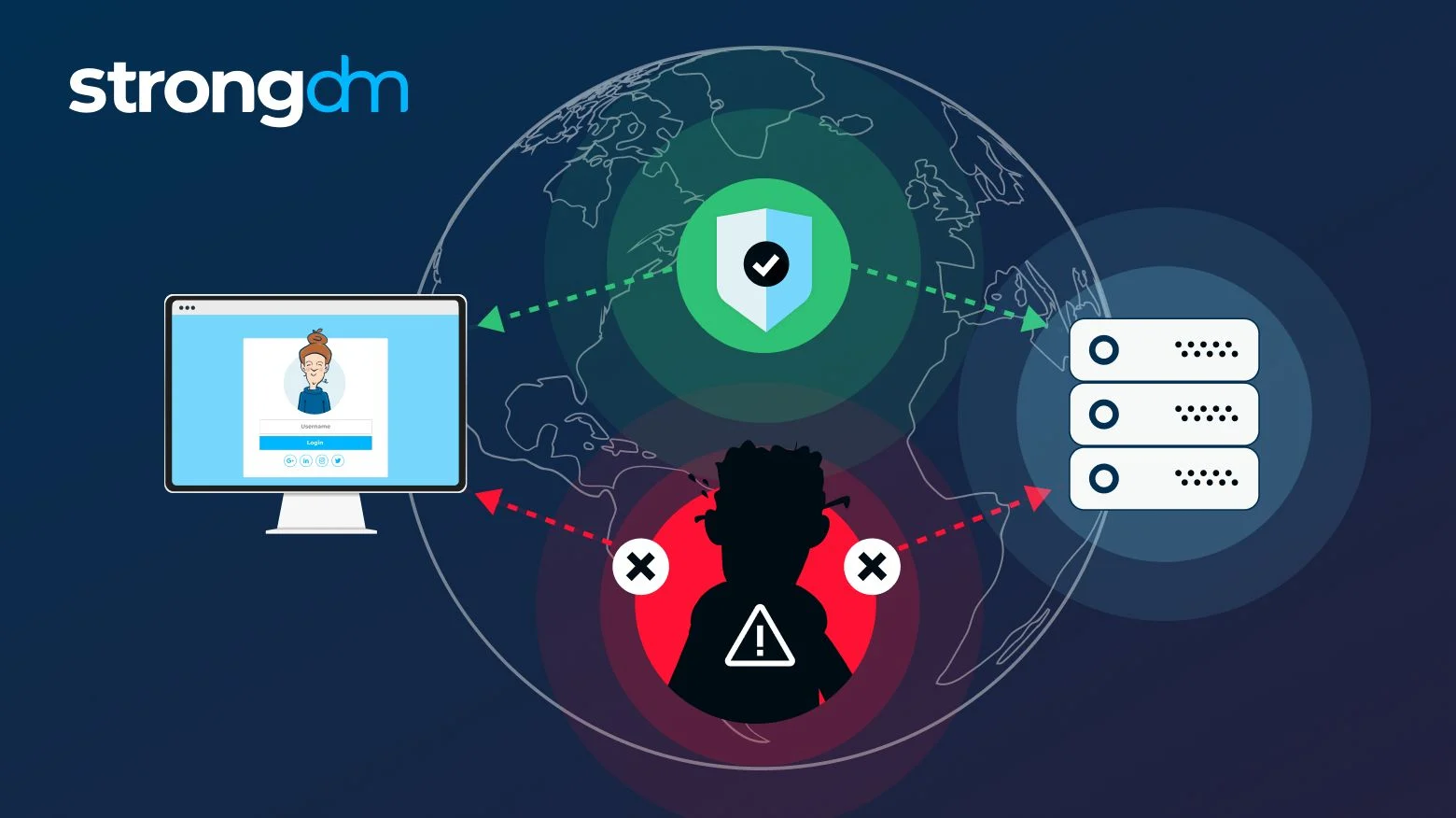
BlueHat 2024: S17: MSTIC - A Threat Intelligence Year in ReviewMMIT, a Norstella company, engaged Seiso to enhance their security program by developing a tailored, risk-based strategy aligned with business objectives. A man in the middle (MITM) attack is a general term for when a perpetrator positions himself in a conversation between a user and an application. Malicious Threats. Cyber attackers use means such as emails and websites to host viruses, phishing scams, malware, exploits and other threats.